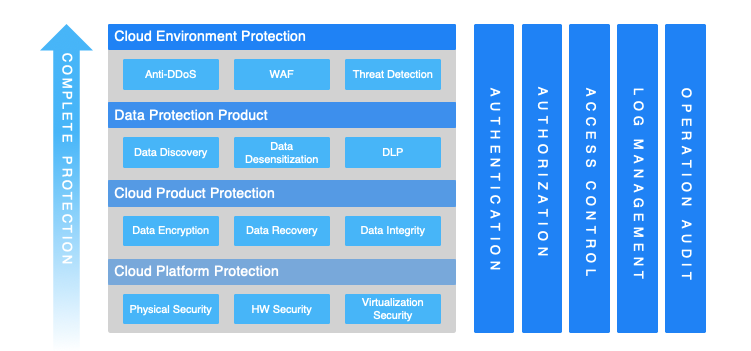
Why Cloud Security Matters
Cloud security is an umbrella term for various measures and technologies that are used to protect cloud-based systems, networks, and data. Without robust cloud security, businesses are vulnerable to cyber threats such as data breaches, ransomware attacks, and unauthorized access. As the adoption of cloud computing increases, so do the risks, making cloud security solutions more essential than ever.
Key Risks in Cloud Security
- Data Breaches: Sensitive customer information and company data could be exposed.
- Insider Threats: Employees or partners with malicious intent may access or alter sensitive data.
- Account Hijacking: Cybercriminals could take over user accounts to steal data or conduct fraudulent activities.
Top Cloud Security Solutions in 2025
Below are the leading cloud security solutions for safeguarding your business’s data.
1. Cloud Encryption Solutions
Encryption is the cornerstone of any strong cloud security strategy. By encrypting your data both at rest and in transit, you ensure that even if it’s intercepted, it remains unreadable without the decryption key.
Benefits of Cloud Encryption:
- Protects Sensitive Data: Encrypting your data ensures confidentiality, whether it’s on a public or private cloud.
- Regulatory Compliance: Many industries require encryption to meet compliance standards like HIPAA or GDPR.
Popular Cloud Encryption Solutions:
- AWS Key Management Service (KMS)
- Microsoft Azure Key Vault
- Google Cloud Key Management
2. Multi-Factor Authentication (MFA)
MFA adds an extra layer of security by requiring users to provide more than just a password to access cloud resources. This could include a fingerprint, a PIN, or a security token.
Why Use MFA?
- Mitigates Account Compromise: Even if credentials are stolen, an attacker cannot access the system without the second factor.
- Increased User Confidence: Employees and customers will feel more secure knowing that their accounts are better protected.
Top MFA Solutions:
- Okta
- Duo Security by Cisco
- Authy
3. Cloud Access Security Brokers (CASBs)
A CASB is a security policy enforcement point between an organization’s on-premises infrastructure and a cloud provider. It allows organizations to monitor and control access to cloud applications and services.
Benefits of Using CASBs:
- Visibility and Control: Gain visibility into cloud activity, including user behaviors and data access.
- Policy Enforcement: Enforce consistent security policies across all cloud platforms.
Popular CASB Solutions:
- McAfee MVISION Cloud
- Microsoft Cloud App Security
- Palo Alto Networks Prisma Cloud
4. Zero Trust Security Model
A Zero Trust model operates on the principle that no one, whether inside or outside the organization, should be trusted by default. Every request, whether it comes from an internal user or external attacker, must be authenticated, authorized, and continuously monitored.
Key Features of Zero Trust:
- Identity and Access Management (IAM): Ensures only authenticated users can access specific resources.
- Least Privilege Access: Users are given the minimum access they need to perform their duties.
Top Zero Trust Solutions:
- Zscaler
- Google BeyondCorp
- Palo Alto Networks Prisma Access
5. Data Loss Prevention (DLP)
DLP technologies help prevent the unauthorized transfer of sensitive information from the cloud to external sources, whether accidentally or maliciously. This is particularly important in industries dealing with highly sensitive data like healthcare and finance.
DLP Solutions Benefits:
- Real-Time Monitoring: Track and control data movement across all cloud applications.
- Compliance Support: Help maintain compliance with data protection regulations.
Top DLP Solutions:
- Symantec DLP
- Digital Guardian
- Forcepoint DLP
Chart: Comparison of Top Cloud Security Solutions
| Security Solution | Key Features | Top Providers |
|---|---|---|
| Cloud Encryption | Data encryption at rest and in transit | AWS KMS, Azure Key Vault, Google Cloud KMS |
| Multi-Factor Authentication | Adds layers of verification for user login | Okta, Duo Security, Authy |
| CASBs | Monitors and enforces security policies on cloud apps | McAfee MVISION, Microsoft Cloud App Security |
| Zero Trust | Strict access control and continuous monitoring | Zscaler, Google BeyondCorp, Palo Alto Networks |
| Data Loss Prevention (DLP) | Monitors and protects sensitive data from leaks | Symantec DLP, Digital Guardian, Forcepoint |
How to Choose the Right Cloud Security Solution
Selecting the right cloud security solution depends on the unique needs of your organization. Here are some factors to consider:
1. Size and Complexity of Your Organization
Larger organizations may require more comprehensive solutions such as CASBs and Zero Trust models, while smaller businesses might focus on encryption and MFA.
2. Industry Regulations
Ensure the solution you choose meets industry-specific compliance standards like HIPAA, GDPR, or PCI-DSS.
3. Cost
Consider both upfront and ongoing costs. Some solutions may offer a subscription model, while others may involve one-time payments.
4. Scalability
As your business grows, your cloud security needs may evolve. Choose solutions that can scale with your business.
Conclusion: Securing Your Cloud Environment
As cyber threats continue to evolve, adopting a multi-layered cloud security strategy is essential. By utilizing top-tier solutions like cloud encryption, multi-factor authentication, and Zero Trust, you can safeguard your digital assets and ensure that your business remains secure in the ever-changing digital landscape.
Remember, cloud security is an ongoing process. Regularly updating your systems and monitoring for potential threats will help maintain a high level of protection for your business. Invest in the right solutions today and keep your cloud environment safe tomorrow.